Remote access technologies have transformed the way we manage and interact with computers from afar. At the heart of this transformation are protocols like Telnet (Telecommunication Network) and RDP (Remote Desktop Protocol ). Understanding the difference between Telnet and RDP is crucial for IT professionals and anyone involved in network administration or remote computing.
This guide explores these differences through five main aspects, highlighting the unique features and functionalities of each protocol.
Table of Contents
TL;DR: Differences Between Telnet and RDP
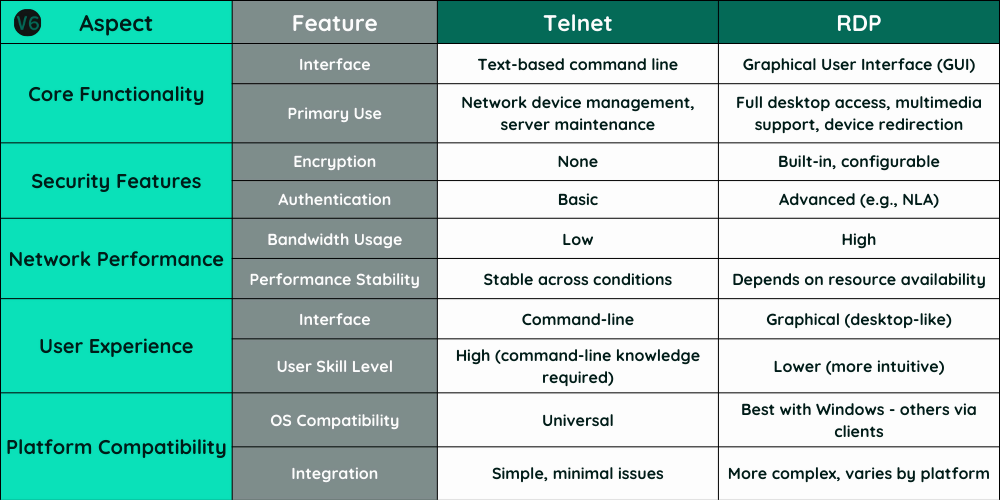
- Functionality: Telnet is text-based, suitable for basic commands; RDP offers a graphical interface for complex tasks.
- User Experience: Telnet requires command-line knowledge; RDP provides a user-friendly graphical experience.
- Performance: Telnet uses less bandwidth, ideal for slow connections; RDP requires more resources, impacting performance in limited bandwidth scenarios.
- Security: Telnet lacks encryption, posing security risks; RDP includes encryption but needs careful security configuration.
- Compatibility: Telnet supports multiple OS with ease; RDP is best for Windows, with challenges on other platforms.

1. RDP vs Telnet: Core Functionality
In the field of remote administration, the core functionality of a protocol determines its applicability in real-world scenarios. Telnet and RDP provide distinctly different approaches to remote access, catering to various needs and environments:
How Telnet Works
- Basic Operation and Command-Line Interface: Telnet provides a simple, text-based interface that allows users to execute commands on remote servers or devices. It operates at a basic level, sending keystrokes as commands and displaying the results as text.
- Typical Applications in Network Administration: Due to its simplicity, Telnet is often used for diagnosing network issues, managing network devices, or environments where graphical bandwidth is not available.
How RDP Works
- Graphical User Interface Access: Unlike Telnet, RDP (Remote Desktop Protocol) provides a graphical user interface (GUI) that allows users to interact with a remote desktop as if they were physically present at the machine.
- Broader Functionality: RDP supports advanced features such as sound, local printer integration, clipboard sharing, and drive redirection, making it suitable for more complex administrative tasks requiring a full desktop environment.
2. RDP vs Telnet: Interface And User Experience
The user interface and ease of use of both Telnet and RDP significantly affect how users perceive and utilize them in different scenarios.
Telnet Interface
- Command-Line Interface: Telnet’s interface is entirely text-based, which requires users to be familiar with command-line operations. This can be challenging for those without technical training.
- Preferred Scenarios: Telnet is often preferred in environments where system resources are limited or when a simple, direct command input is adequate—such as in server maintenance and basic file operations.
RDP Interface
- Rich User Experience with GUI: RDP offers a graphical user interface that resembles using a local computer, which can be easier for users without command-line skills.
- Significant Advantages: The GUI of RDP makes it ideal for more complex tasks that involve software with graphical output, detailed document editing, or other interactive tasks.
3. Network Performance and Resource Usage
Understanding how Telnet and RDP impact network performance and their resource demands is crucial for ensuring efficient remote access without compromising system or network integrity.
Telnet Uses Less Resources
- Low Bandwidth Usage: Telnet uses minimal bandwidth because it only transmits text. This makes it efficient even on low-speed internet connections.
- Performance in Various Network Conditions: Telnet performs reliably across different network conditions due to its low data transmission needs, which minimizes latency and speed issues.
RDP Requirements Are Higher
- Higher Bandwidth and Resource Requirements: RDP requires more bandwidth because it transmits graphical data, which is much larger than text. This can strain network resources, especially in bandwidth-limited environments.
- The heavy data usage of RDP can lead to slower performance under certain conditions. Optimizing RDP settings, like adjusting image quality and disabling certain features like sound and printer sharing, can help manage its impact on network resources.
4. RDP vs Telnet: Security Features
Security is a common concern when accessing systems remotely. Both Telnet and RDP offer security features with differences that are essential to understand for secure deployment and use.
Telnet Security
- Lack of Encryption: Telnet does not encrypt data, which means that all information, including sensitive data like usernames and passwords, is transmitted in clear text. This can lead to security breaches if the data is intercepted.
- Historical Context: Originally designed when security threats were less severe, Telnet’s use today is limited to specific, controlled environments or replaced by more secure protocols like Secure Shell Protocol (SSH).
RDP Security
- Built-in Encryption and Additional Security Settings: RDP includes encryption capabilities to secure data transmissions. It also allows for the use of Network Level Authentication (NLA) and other security measures to protect against unauthorized access.
- Potential Vulnerabilities: Despite its advanced security features, RDP can be vulnerable to attacks if not properly configured. Additional settings like residential IPs for RDP, disabling clipboard sharing and using strong passwords are essential for securing RDP sessions.
5. Platform and Software Compatibility
Compatibility with various operating systems and platforms can dictate the choice between Telnet and RDP based on the infrastructure already in place.
Telnet Compatibility
- Universal Support: Telnet works on nearly all operating systems, including various versions of Unix, Linux, Windows, and even embedded systems, without needing any special adaptations.
- Modern OS Integration Limitations: Despite its wide compatibility, Telnet’s integration into modern operating systems can be limited by security concerns and newer protocols with better security.
RDP Compatibility
- Primary Design for Windows: RDP was specifically designed for Windows environments, providing seamless integration and functionality within those systems.
- Challenges and Solutions for Non-Windows Platforms: While RDP clients are available for other platforms like macOS and Linux, they may encounter integration challenges. Solutions often involve third-party clients or configuring RDP settings to ensure compatibility.
- Tags:
- comparison


